Automated Threat Hunting & Response....
Alpha XDR assumes that their client networks are already compromised and implement an army mindset of offense-based strategy. In this methodology, Alpha XDR think like the adversary and deploy the same tactics, techniques, and procedures that the adversary uses against their target. Alpha XDR Automated hunting techniques hunt for adversaries within the network in regular intervals.
Alpha XDR hunting technique actively identify adversaries without known indicators of compromise, and detecting them before data is exfiltrated or systems are disrupted. Alpha XDR’s offense-based approach enables security analysts to overcome the most common challenges with traditional defences in detecting sophisticated adversaries. The challenges which automated hunting combats are:
Attackers evading traditional tools
Alpha XDR’s hunting rules destroys the traditional defense on primitive perimeter tools which are easily evaded by the attackers using advanced techniques, tactics & procedures.
Combat Polymorphic Malware attacks
Alpha XDR combats sophisticated attacks in form of never-before-seen tools and tactics including custom and polymorphic malware that defeats detection strategies.
Continuous Hunting
Alpha XDR have industry experienced security analysts who are highly talented and provide a constant vigilance in threat hunting which is one of the main concerns for enterprises and companies today.
Automated Hunt
Alpha XDR can deploy automated threat hunts across entire dataset thus empowering the hunt. Through automation analysts detect and evict adversaries at all stages of the kill chain before damage and loss occurs.
Alpha XDR enables automated investigation and response directly within the platform. This automation is built on top of bi-directional integrations, data management, and customizable analytics.
Alpha XDR’s Playbooks can be simple single-threaded logic flows or something more complicated with multiple conditions and actions.
There are practice playbooks options as well which run’s in production or either use as a starting point for your operations. Easy-to-use playbooks with advanced customizability built directly into the platforms.
24/7 Threat Detection and Response
Alpha XDR protects customer networks round the clock using multi-modal detections to find known and unknown threats, then correlates threats together automating much of the threat investigation process. Anomaly based detections are continuously baselined across organisation.
- Flexible Data Sourcing: Collect data from any security product, IT and Productivity tool using pre-built integrations
- Sensor- Driven Data Collection: Collect raw network and log data to identify additional threats
- Data Normalization and Enrichment: Data automatically normalized and enriched to enable comprehensive data analysis.
- Automated Threat Hunting: Schedule repeatable threat hunts across entire dataset.
- Multi-Mode Threat Detection: Combines Static rules, supervised and unsupervised machine learning and automated threat hunting to identify advanced threats.
- Machine Learning Correlation: Creates Corelated incidents providing security analysts prioritised threats to investigate.
- Guided Investigation: Complete investigation faster using built-in context, increasing efficiency and effectiveness
- Direct Incident Response: Schedule repeatable threat hunts across entire dataset.
Our expert researchers validate the incidents which are contextually rich in threat intelligence and adversary techniques correlated with MITRE techniques. The XDR alert comes with a personalized description of what happened, the impact, and the potential resolution.
Alpha XDR continuously trains its models with real and simulated data to stay up to date 24/7 threat detection and response actions.
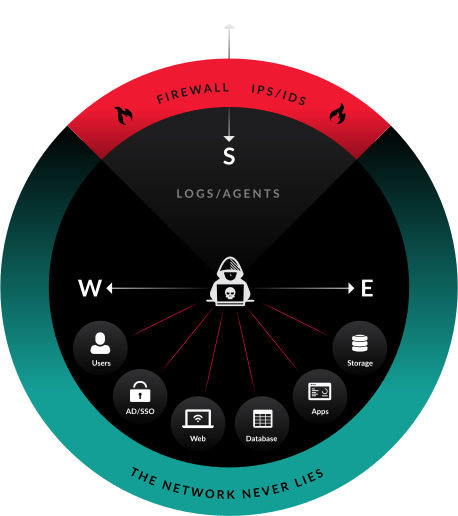
Managed Detection & Response (MDR) Services
Alpha XDR platform combines the critical security capabilities and automation which needs to deliver unique services without adding staff to security operations teams thus delivering a Managed Detection & Response service.
Alpha XDR is a multi-layer multi-tenant open XDR platform which delivers security to multiple clients from one single platform and one single UI. This allows to manage thousands of end customers with a single license designed with multi-tenancy built-in.
The MDR services allows integration with every major Endpoint Detection & Response and provide flexibility to customers without the need to change their existing technology stack.
- Intelligent Multi-Tenancy : This ensures no commingling of customer data while enabling security analysts to service multiple customers easily with the Alpha XDR approach to smart multi-tenancy.
- Ultra-Flexible Data Sourcing: Incorporate data from any existing security control, IT, and productivity tool into Alpha XDR using pre-built integrations.
- Sensor-Driven Data Collection: Use the Alpha XDR sensors to collect the raw network and log data from customers to identify additional threats not seen by their existing security stack.
- Easy Customization: Alpha XDR can help create dashboard, reports, automatic threat hunting rules, etc. to provide differentiated services to its customers
- Machine Learning Correlation: Using graph machine learning techniques, alerts are combined into prioritized incidents ready for investigation.
- One single License: Eliminate commercial complexity with our one platform, one license approach.
- Drive Unseen SOC Productivity: Drive increased efficiency across your security operations team, enabling customer growth without adding staff.
Industrial /OT Cybersecurity
Industrial /OT Cybersecurity

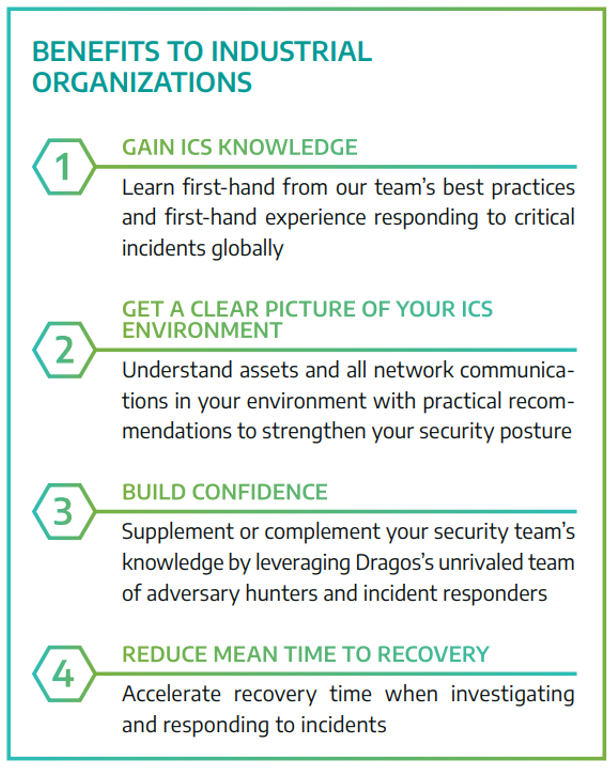
Our expert services team provides industrial organizations with the full spectrum of cybersecurity services to deliver visibility and insight into ICS/OT environments, educate practitioners, mitigate risks, and uncover and respond to threats.
Our Services....
Our Services and Engineering packages are performed by an experienced team who excels in OT Cybersecurity and compliance adherence like IEC 62443, NERC CIP, NIST 800-82
| SERVICE | DESCRIPTION |
| Cyber Physical Asset Management & Visibility | Problem: Cyber assets (remote terminal units, protection relays, automation controllers, switches, radios, firewalls, etc.), most of which are unique to the power industry, become vulnerable over time and have software bugs that can negatively impact the operating power system. If left unaddressed these vulnerabilities offer an attack vector for malicious actors and can result in hefty fines from regulatory bodies. Solution: Through customizable options that fit your current need, you will be provided with summary reports, instant notification, and dashboards outlining the health of your cyber assets and your overall security posture. These deliverables offer the peace of mind knowing that your system is up-to-date, compliant, and protected from malicious actors as well as free of software bugs that can decrease the operational reliability. |
| ARCHITECTURE REVIEW Evaluate Your Existing Security Program |
|
| NETWORK VULNERABILITY ASSESSMENT Close Gaps In Network Defense |
|
| THREAT HUNTING Expose Undiscovered Threats |
|
| INCIDENT RESPONSE Rapid Onsite and Offsite Support |
|
| Vulnerability Management |
|

