//ALPHA XDR ADVANTAGE
Security Operations Centers (SOC) Automation
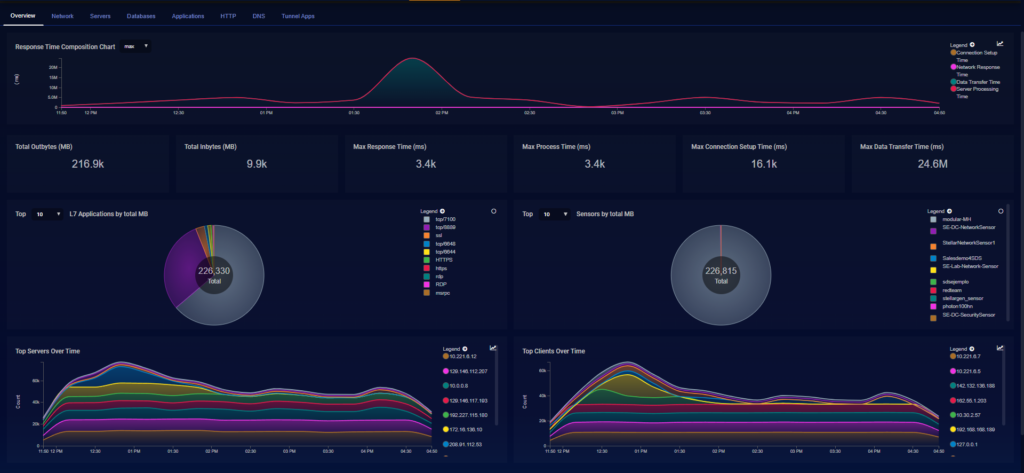
Alpha XDR expertise automated to augment the SOC as a virtual analyst. 100% of events investigated at machine speed, scale and consistency – all in the context of Alpha XDR’s frontline intelligence.

Network Detection & Response (NDR)....
Alpha XDR deploys Network Detection & Response (NDR) through the network sensors to perform deep packet analysis of the network traffic. The network traffic detected through NDR are checked with behavioural monitoring techniques for any network anomaly or suspicious traffic. The main advantage of the NDR solution is that it adds an added layer of security in the security technology stack monitoring both East-West and North-South traffic. The NDR sensors further bring in the visibility for the network assets which are placed at the furthest corner of the network.
Another advantage of the NDR’s are in the area of threat remediation and containment. ALPHA XDR’s Network Detection and Response allows automated threat remediation based on the detected threat and their respective indicators of compromise integrated with playbook which could be executed from predefined rules.
With the deployment of NDR, it can detect malicious activities in the network without the need to install a standalone agent in the devices. This approach becomes very useful in the Operational Networks which are mostly running legacy systems and can’t support agent installations for their protection.
Alpha XDRs NDR serves as a compensating control and protects the critical network assets which are the primary target of the threat actors.
Cloud Protection Sensors....
Alpha XDR’s supports new level of visibility including Cloud IaaS and SaaS applications like O365 & G-Suite. security software-based sensors include a DPI engine, so it can collect the right metadata from traffic in the cloud via the native interfaces provided by cloud providers like VTAP in Azure or VPC Traffic Monitoring in AWS.
Threat Hunting–Internet Security, Network Security and Cloud Security In One Platform:
| Alpha XDR Detection & Response Capability | Protect SaaS Apps | Secure Public Cloud Infrastructure |
| Collect, transform and store events | ✅ | ✅ |
| Automatically detect many attacks including account takeover | ✅ | ✅ |
| Perform both manual and automatic threat hunting | ✅ | ✅ |
| Auto discover assets and correlate events | ✅ | ✅ |
| Provide Compliance Reports | ✅ | ✅ |
| Provide full visibility across SaaS apps, VPC, endpoints and networks through Open XDR | ✅ | ✅ |
| Collect, transform and store events for AWS public cloud | ✅ | |
| Provide powerful Network Traffic Analysis for AWS/Azure VPC traffic | ✅ |
Endpoint Detection & Response (EDR)....
An EDR is a critical part of the security stack, but on its own, it does not realize the goal of XDR, which is to defend the entire attack surface cohesively. Alpha XDR supports all the major EDR‘s to give your team consistent and performant results and provide the required flexibility as well.
Alpha XDR capability allows you to turn your EDR (or EDRs if you have multiple vendors) into XDR instantly. Integrated EDRs are brought to their fullest potential by improving the underlying fidelity of data from the EDR, and then correlating it with telemetry from the rest of the attack surface. You can Command your EDR (or EDRs) from one platform alongside all of your other security controls; future-proof your security stack without fear of operational downside.
Alpha XDR uses deduplication method into the EDR alerts. The “Deduplication” technique applies Machine Learning to identify source EDR alerts that are duplicative and likely part of the same activity, and generates a single alert within Alpha XDR to improve automation and analyst performance.
Automated Threat Hunting....
Alpha XDR can deploy automated threat hunts across the entire dataset thus empowering the hunt. Through automation, analysts detect and evict adversaries at all stages of the kill chain before damage and loss occur. Threat hunting without automation is impractical for most of the organisations.
Alpha XDR Automating threat hunting can help accelerate organisations’ network security process, reduce operating costs and improve capacity to mitigate advanced cybersecurity threats in time.
Automated Threat hunting of Alpha XDR covers the execution in a short duration which would otherwise take days to perform. Using ALPHA XDR automated threat hunting security teams may have the advantage and the necessary capabilities to stay ahead of the growing array of sophisticated security threats and help secure the network from cyber attackers.

Automated Response....
Alpha XDR define and execute responses from the same platform detections to dramatically minimize attack dwell time. Many response actions ranging from containing a host to blocking on a firewall to sending any webhook APIs.
Getting Started....
Improve security efficiency and reduce business risk with automated alert triage, investigation and prioritization. Contact us for a demo today.
Integrated Reasoning – How Automated Defense Makes Decisions
Learn how Automated Defense uses data science and security expertise to emulate the decision- making of skilled security analysts.
Components and Architecture of Automated Defense
Learn how Alpha XDR Automated Defense augments your Security Operations Center in our latest white paper.
Key Features....
Improve security efficiency and reduce business risk with automated alert triage, investigation and prioritization. Contact us for a demo today.
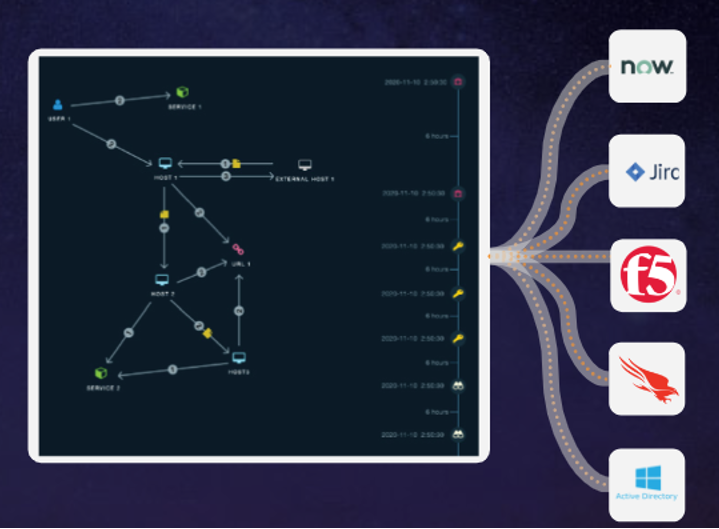
Deep Integrations Across Critical Tool Categories
Alpha XDR not only collects telemetry from organisations existing and security tools but can respond back through those same tools to scale your operations and reduce MTTR. Respond through firewalls, EDR, IAM, ticketing systems, messaging apps and more. If you need more complex orchestration, Stellar Cyber integrates with numerous SOAR products like Phantom, Demisto, Swimlane and Siemplify.
Respond Directly from an Investigation
Alpha XDR keeps response actions at the analyst fingertips at all times. While investigating an incident, or hunting for suspicious activities, a security analyst can directly respond in the same console. So if you identify an asset with suspicious outbound communication, you can directly contain that host without navigating away from your current view.
Fully Automated
Set up Automated Threat Hunting playbooks to take a response action based on any criteria. Automate away mundane work to keep your people focused on what they do best while responding to alerts at machine speed.

