HOW ALPHAXDR RESPONDS TO CYBERSECURITY
INCIDENTS
How to Respond to Cybersecurity Incidents
It’s occurred: You’ve received a breach notification — from internal teams, an external
informant, or law enforcement. Unauthorized individuals have bypassed your security
and gained access to your organization’s systems. What will your next steps be?
Take the example of Deloitte, which recently issued a statement in response to claims
by the ransomware group Brain Cipher, who allegedly stole a substantial amount of data
from the company. Brain Cipher, a hacking group that emerged in April 2024, listed
Deloitte UK on its Tor-based website, claiming to have obtained over one terabyte of
data. They’re threatening to release the stolen files unless a ransom is paid within five
days. Deloitte responded with a statement, asserting that the incident involves a single
client’s system, which is outside the company’s network. They emphasized that no
Deloitte systems have been impacted.
The company’s statement reflects a controlled and cautious approach, trying to ensure
that the incident is handled responsibly, keeping public communication clear and
concise. This response contrasts sharply with earlier, more infamous breaches, such as
the Equifax breach, where CEO Rick Smith made a statement that would later be
overshadowed by the mishandling of customer claims. Similarly, Uber’s attempt to
cover up a breach by paying hackers only added to the controversy, and Travelex’s poor
handling of a ransomware attack in 2020 led to significant backlash for attempting to
disguise the event as “scheduled maintenance.”
In the context of Deloitte’s breach, the company is facing a choice: Will it prioritize
transparency and a timely response, or will it fall into the trap of mismanagement that
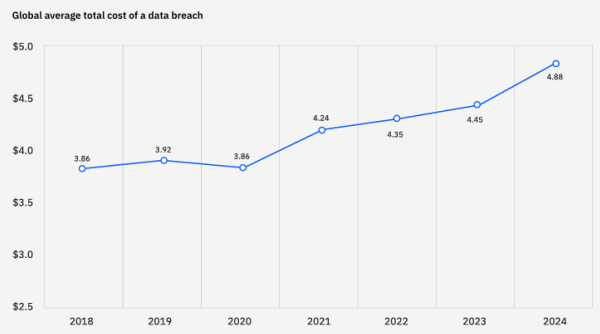
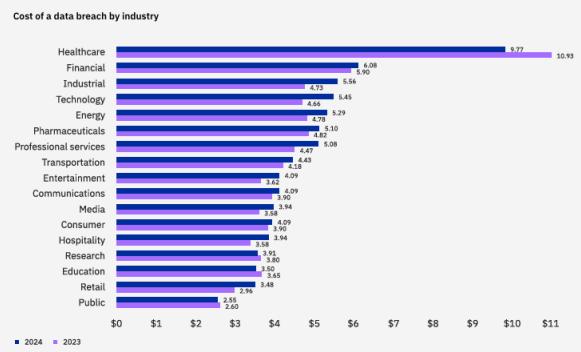
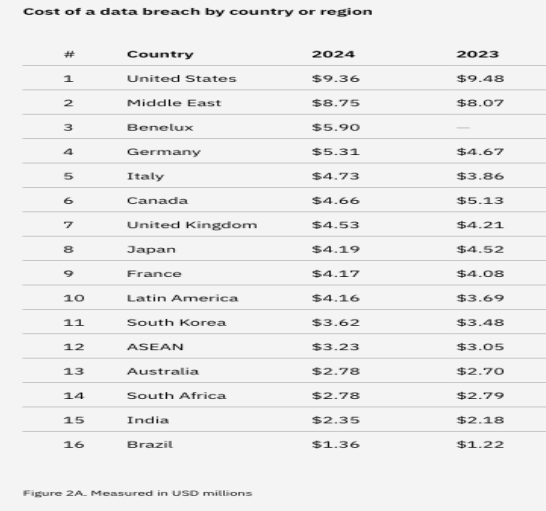
has plagued other organizations? The stakes are high. With the average cost of a stolen
record topping $429 in 2019, organizations must develop a comprehensive incident
response strategy to prevent breaches and mitigate the damage when an attack occurs.
This strategy includes not only tools to detect and respond to active threats but also
clear measures for managing the aftermath of a breach.
Deloitte’s prompt and transparent communication about the breach illustrates the
critical importance of maintaining a strong incident response plan and shows that how
a company responds to a cyberattack can have far-reaching consequences for its
reputation and trustworthiness.
Cybersecurity Database Incidents
A data breach impacts far more than just records containing sensitive customer and
partner information or critical financial data. It sets off a cascade of damaging
consequences, including the theft of intellectual property, harm to brand reputation and
value, increased vulnerability to subsequent cyberattacks, and potential legal action
from affected parties.
An effective incident response program aims to minimize the damage and restore
normal operations as swiftly as possible. Additionally, a comprehensive response
strategy includes an investigative element, allowing organizations to identify the root
causes of the breach and gain insights to strengthen their defences against future cyber
threats.
Incident Response Lifecycle
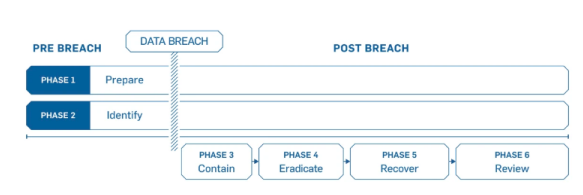
Six Components of Working Incident Response Plans
Non-government and public entities operating in the field of cybersecurity, including
leading researchers at the SANS Institute (SysAdmin, Audit, Network, and Security
Institute) and the U.S. National Institute of Standards and Technology (NIST) define six
steps involved in the creation and implementation of a successful incident response
plan
The incident response phases are:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
Preparation
This phase will be the work horse of your incident response planning, and in the end, the
most crucial phase to protect your business. Part of this phase includes:
Ensure your employees are properly trained regarding their incident response roles and
responsibilities in the event of data breach
Develop incident response drill scenarios and regularly conduct mock data breaches to
evaluate your incident response plan.
Ensure that all aspects of your incident response plan (training, execution, hardware
and software resources, etc.) are approved and funded in advance
Your response plan should be well documented, thoroughly explaining everyone’s roles
and responsibilities. Then the plan must be tested in order to assure that your
employees will perform as they were trained. The more prepared your employees are,
the less likely they’ll make critical mistakes.
Identification
This is the process where you determine whether you’ve been breached. A breach, or
incident, could originate from many different areas.
Containment
When a breach is first discovered, your initial instinct may be to securely delete
everything so you can just get rid of it. However, that will likely hurt you in the long run
since you’ll be destroying valuable evidence that you need to determine where the
breach started and devise a plan to prevent it from happening again.
Instead, contain the breach so it doesn’t spread and cause further damage to your
business. If you can, disconnect affected devices from the Internet. Have short-term
and long-term containment strategies ready. It’s also good to have a redundant system
back-up to help restore business operations. That way, any compromised data isn’t lost
forever.
This is also a good time to update and patch your systems, review your remote access
protocols (requiring mandatory multi-factor authentication), change all user and
administrative access credentials and harden all passwords.
Eradication
Once you’ve contained the issue, you need to find and eliminate the root cause of the
breach. This means all malware should be securely removed, systems should again be
hardened and patched, and updates should be applied.
Whether you do this yourself, or hire a third party to do it, you need to be thorough. If any
trace of malware or security issues remain in your systems, you may still be losing
valuable data, and your liability could increase.
Recovery
This is the process of restoring and returning affected systems and devices back into
your business environment. During this time, it’s important to get your systems and
business operations up and running again without the fear of another breach.
Lessons Learned
Once the investigation is complete, hold an after-action meeting with all Incident
Response Team members and discuss what you’ve learned from the data breach. This
is where you will analyze and document everything about the breach. Determine what
worked well in your response plan, and where there were some holes. Lessons learned
from both mock and real events will help strengthen your systems against the future
attacks
It’s important to note that not every cyber-attack is a cybersecurity attack. An
organization could fall victim to a Denial-of-Service (DoS) or Distributed Denial-ofService (DDoS) attack, which aims to disrupt operations and connections to external
systems. However, these attacks are not primarily targeting sensitive corporate data or
personal information.
A cybersecurity attack, on the other hand, specifically targets sensitive data, such as
corporate secrets or personally identifiable information (PII) of customers. A common
example of a cybersecurity attack is a ransomware attack, where a threat actor installs
malware that encrypts critical systems and data storage devices, holding them hostage
until a ransom is paid.
When a cybersecurity attack is detected, the response process is divided into four key
steps for the incident response team to follow:
- Step 1: Identify the type and scope of the cybersecurity incident.
- Step 2: Define specific objectives and conduct a detailed investigation.
- Step 3: Take timely and appropriate action.
- Step 4: Recover systems, data, and networks.
Each of these steps involves a dynamic series of sub-steps, which are tailored based on
the specifics of the incident as it unfolds.
In the initial identification phase, the IT security team must address several critical
questions to manage the incident response effectively:
- Who is responsible for the attack?
- What is the scope and impact of the attack?
- When and how did the attack occur?
- What data or systems did the attacker access?
- Why did they launch the attack?
One of the most urgent tasks after detecting a data breach is pinpointing the entry point
used by the attacker and understanding how the breach is impacting operations.
Additionally, it’s crucial to quickly determine what information has been stolen, deleted,
encrypted for ransom, or exposed to unauthorized third parties. This means that during
the identification phase, the team must thoroughly investigate which systems,
networks, and data assets have been compromised.
Once the incident response team has identified the key characteristics and scope of the
breach, corrective actions must be taken to contain the threat and eventually remove it.
During the containment phase, the IT security team can implement various measures
such as:
- Blocking unauthorized access to resources.
- Restricting entry points, including email addresses, malicious websites, or
infected devices/systems. - Closing specific communication ports and mail servers.
- Changing system administrator credentials, prioritizing systems most vulnerable
to attack. - Applying targeted firewall filtering rules.
- Moving website home pages and switching to backup hosting.
- Isolating affected systems and network segments as needed.
During containment, the IT team should also update and patch all systems and
endpoints, reviewing power-user access rights and login credentials to ensure all areas
are secured.
Once the malware has been contained, the eradication phase begins, where the focus
shifts to identifying and eliminating the root cause of the breach. This process includes:
:
- Identifying all affected systems and devices both within and outside the
organization to fully remediate the threat. - Conducting a detailed malware analysis.
- Monitoring for any responses or further actions from the attackers.
- Implementing a defense strategy in case the attackers attempt to expand their
attack with additional methods or malicious code. - Ensuring the network is fully secure to prevent any follow-up attacks once the
initial threat has been neutralized.
Throughout this phase, the cybersecurity team must carefully document all malware
actions and maintain a proper chain of evidence.
It is crucial for organizations to keep accurate records of all relevant evidence, including
the location, serial number, model number, hostname, MAC addresses, and IP
addresses of affected devices or those used during the remediation of the cyberattack.
The recovery phase follows the eradication stage and ensures the organization returns
to normal operations while minimizing the risk of any ongoing threats. Key recovery
steps include:
- Restoring infected systems from clean backups and trusted sources.
- Replacing compromised files with the most recent backup versions.
- Gradually lifting restrictions imposed during the containment phase.
- Forcing password resets on compromised accounts and changing all
administrator credentials. - Installing necessary software updates, patches, and adapting firewall rules.
- Conducting comprehensive security checks on all systems and networks to
confirm they are secure and fully operational.
These steps are essential to ensure that systems are restored and protected from future
breaches.
Once all systems are back to normal and there is no immediate risk of further attacks,
the organization may decide to conduct a penetration test and a compromise
assessment to verify the integrity of its systems and controls within the perimeter.
Following this, a thorough follow-up analysis, often referred to as the “Lessons Learned”
phase, should be conducted. This stage allows stakeholders to review the entire
incident and address several important questions, such as:
:
- How did employees and management respond to the breach, and how well did
they follow the established security procedures? - What changes are needed in the cybersecurity policies and procedures?
- What weaknesses allowed the attacker to breach the perimeter, and could this
have been prevented? - What additional training is necessary, and in which areas?
- What steps will be taken to prevent future cybersecurity incidents, and what are
the key lessons learned from this data breach?
The specific steps taken during each phase will depend on the nature of the threat, the
organization’s incident response strategy, and the tools used to detect and address
cyber threats. However, all security incidents follow the six core stages of the incident
response framework, and most of the actions described above are essential elements
of each stage.
For example, the U.S. National Institute of Standards and Technology (NIST) provides a
recommended incident-handling checklist for managing a data breach, which
organizations can adapt to their specific needs
Incident Handling Checklist
When dealing with cybersecurity incidents, it’s essential to categorize and prioritize
each incident based on its severity to ensure proper and timely response.
Prioritization is Critical for Incident Response Management
Given that security incidents have become a routine challenge for IT security teams,
particularly in large and multinational organizations, responding to them should not be
done on a first-come, first-served basis. Incident response should follow strict
procedures for categorizing incidents based on clear criteria, such as functional
impact, information impact, and recoverability.
Functional Impact Incident Priority
Cyber-attacks typically target the functionality of an organization’s systems, aiming to
disrupt normal business operations. Such attacks affect both internal users and
customers relying on those systems.
The incident response team should quickly assess the immediate impact of the incident
and determine the potential long-term functional consequences if containment isn’t
achieved quickly.
Information Impact Incident Priority
The information impact of a data breach can be broad, affecting aspects like data
confidentiality, integrity, and availability. While exfiltration of sensitive data is a primary
goal for most attackers, others may alter or encrypt information, such as through
ransomware attacks.
The incident response team should prioritize identifying the affected information and
assess how the breach impacts third parties, including customers, partners, and other
stakeholders.
Cybersecurity Incident Recoverability
An effective incident response strategy cannot precisely predict the time and resources
required to contain and recover from an incident. Therefore, the severity of an incident
in terms of recoverability depends on the nature of the attack and how successful it is.
Some attacks, particularly those involving the theft and misuse of confidential
information, may be non-recoverable. In these cases, the IT security team should focus
on forensic analysis to understand the breach and implement measures to prevent
future incidents, rather than focusing on a full recovery.
Many incidents also require the expertise of third-party specialists to fully contain,
eradicate, and recover from the threat, as organizations may lack the necessary internal
resources.
Thus, the incident response team must carefully evaluate recovery options before
deciding how to handle the situation.
The Importance of Prioritizing Cybersecurity Incidents
Prioritizing cybersecurity incidents is crucial for ensuring appropriate responses. It
helps organizations allocate the right resources to manage specific incidents based on
their severity.
Challenges in Incident Response Handling
Advanced Persistent Threats (APTs) represent a major challenge in incident response.
These sophisticated, continuous cyberattacks are not only directed at government
agencies or critical infrastructure but also target businesses, including small and
medium-sized enterprises (SMEs) and non-governmental organizations.
Malicious actors now have access to powerful tools, including hacking software,
malicious code, and social engineering techniques. The primary difference between
various cyberattacks often lies in the attackers themselves—whether they are statesponsored, part of a large organized crime syndicate, or a small group of hackers.
While smaller hacking groups can still cause significant damage, nation-state attackers
and major criminal organizations may operate undetected for months or even years,
exfiltrating sensitive data and sabotaging operations over an extended period.
Few organizations are fully equipped to handle a major cybersecurity incident
independently. The lack of skilled talent, gaps in processes, and limited knowledge
about the latest cyber threats and attack methods make it difficult to respond
effectively.
Additionally, many organizations cannot identify the type of attack they are facing until
an external cybersecurity expert conducts a thorough investigation. The sheer volume
and complexity of evolving cyber threats often overwhelm internal IT teams.
Alarmingly, many organizations fail to implement even basic cybersecurity practices,
such as patching vulnerabilities or updating outdated business software, despite
knowing these are major attack vectors exploited by cybercriminals.
Conclusion
No organization is immune to cybersecurity incidents, whether minor or major. The
pressure is mounting on Chief Information Officers (CIOs) and Chief Information
Security Officers (CISOs) to adopt robust cybersecurity defenses and craft
comprehensive incident response plans.
While strengthening perimeter defenses is one approach, organizations must also plan
for protecting sensitive data in a compromised environment—by having a solid incident
response strategy in place.
A key part of this strategy involves using tools like ALPHAXDR Active Defense to detect
and respond to threats as early as possible, preventing escalation. By leveraging
cybersecurity intelligence, data analytics, process monitoring, and user behavior
analysis, organizations can form the backbone of an effective IT security strategy.
Evolving from a static cybersecurity model to a dynamic one, capable of addressing
emerging cyber threats, is crucial for any organization aiming to stay ahead of risks.
Additionally, cultivating a culture of cybersecurity awareness is fundamental to ensuring
the success of an incident response strategy.
TAKE THE NEXT STEP: CREATE OR FORTIFY YOUR PLAN WITH AlphaXDR
AlphaXDR provides pre- and post-incident response services to proactively defend
against and respond to cyber incidents. Both before and after a breach, our advanced
threat detection and response capabilities, powered by the AlphaXDR platform, offer a
comprehensive approach to cybersecurity.
AlphaXDR’s platform integrates a broad range of security data sources, including
network traffic, endpoints, and cloud environments, enabling real-time threat detection
and rapid response. With the help of our expert security analysts, incident responders,
threat hunters, and malware researchers, we assist organizations in quickly identifying
and mitigating breaches, while also implementing strategies to prevent future incidents.
Key features of AlphaXDR include:
- Comprehensive Threat Detection: Combines multiple data sources (network,
endpoint, cloud, and more) to provide a unified view of potential threats. - Automated Incident Response: Quickly contain and remediate incidents using
automated workflows, reducing response times and human error. - Advanced Threat Hunting: Proactively search for hidden threats and anomalies
using powerful analytics and machine learning. - Seamless Integration: Easily integrates with existing security tools, providing
enhanced visibility without requiring a full overhaul of your security
infrastructure. - Real-time Analytics and Reporting: Offers detailed insights and actionable
intelligence with real-time alerts, helping teams make informed decisions
quickly. - Extended Detection and Response (XDR): Offers a cross-layered approach to
security, detecting threats across endpoints, networks, servers, and cloud
environments for a holistic defense.
AlphaXDR has worked with organizations to address some of the most challenging
intrusions and malware attacks in recent years, helping businesses strengthen their
defenses and respond effectively to cybersecurity incidents.

